Introduction:
Cybercrime is generally said as an unlawful act where any crime involves a computer and a network, Here computer might be used in committing the crime, or it may be the target that may harm someone’s security or finances. It usually consists of activity like financial crimes, e-mail spoofing, forgery, cyber defamation, cyber stalking, intellectual property crime, online gambling, pornography, forgery, and sale of illegal articles, it covers a wide range of different attacks, which all deserve their unique approach when it comes to improving our computer’s whether it’s personal or office computer.
In 2014, CNNMoney reported that almost half of American adults had been hacked that year alone.
In 2015, cyber-crime was responsible for 53% of all crime in the UK
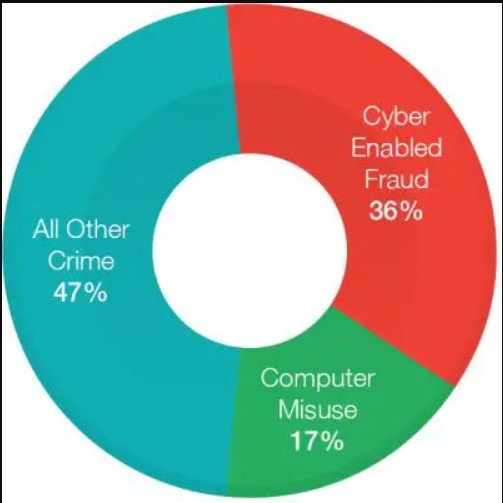
That may seem hard to believe but figures show that 556 million people are victims of cybercrime—on average that’s 1.5 million victims per day.
It is believed cybercrime could end up costing billions of dollars of damage, which only stresses the need for stronger security systems and better computer education for those connected to the internet. It also stresses the need for consequences for hackers who create security breaches.
A recent example of a cyberattack and the following legal action is the case of Lauri Love. Love is a British cyber activist who’s been accused of penetrating systems belonging to the FBI, the US Navy, and the Federal Bank.
Just days ago, a British judge ruled that Love could be extradited to the United States for trial.
Love is accused of multiple counts of “computer misuse” under British law. If successfully extradited to the United States, he will go to trial for crimes that could sentence him to up to 99 years in prison. Love’s case demonstrates the extent of response that governments are beginning to take when they believe their systems have been compromised.
we often hear the term ‘cybercrime’ bandied about nowadays, as it’s a greater hazard now than at any other time because of the sheer number of associated individuals and gadgets. Criminals committing cybercrime use several methods, depending on their skill set and their goals. Here are some of the different ways cybercrime can take shape:
- Theft of personal data
- Copyright infringement
- Fraud
- Child pornography
- Cyberstalking
- Bullying
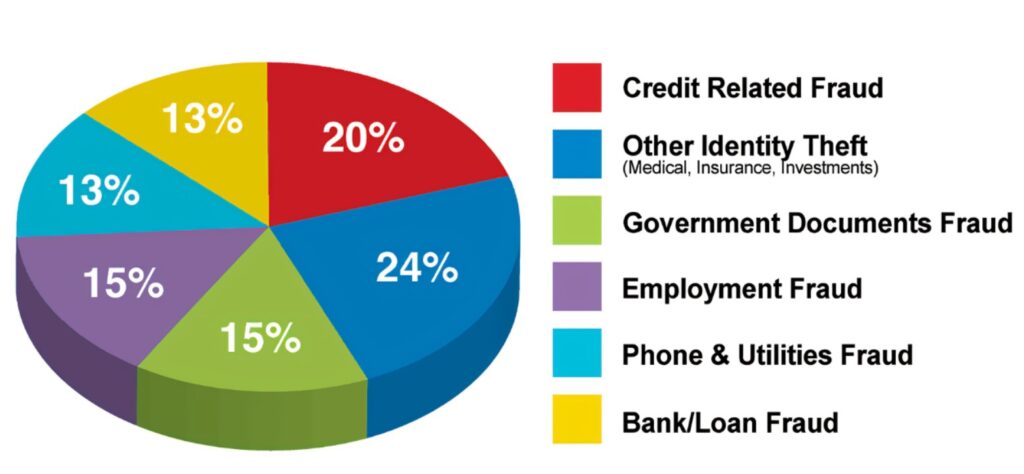
According to some estimations, nearly two-thirds of companies say they have been the victim of a cyberattack in the past year. The economic impact of these attacks is significant, costing the global economy about $445 billion every year, and it will only get worse. This trend has highlighted the need for companies to protect data and ensure business continuity in today’s increasingly connected world. Security teams need access to information they can use to identify, assess and respond to threats, and companies must better understand the evolving landscape of cyber threats, identify vulnerabilities in their systems and develop effective mitigation strategies.
Cybercriminals:
They are typically teams of skilled criminals targeted on control, power, and wealth. These criminals are extremely subtle and organized, and should even give crime as a service. These attackers are usually profoundly prepared and well-funded.
These days, almost all cybercrime is carried out by organized groups. The solo hacker is essentially a thing of the past. Even script kiddies operate in small groups. The largest and most sophisticated attacks require the skills of dozens or even hundreds of attackers. The most prolific cybercriminals have become segmented by expertise and collaborate with other hackers or criminal groups. These groups have evolved over the past few years, becoming more audacious and cleverer. They function exactly like corporations. Organisations may better identify their actual cybercrime attack surface and risk of assault by understanding what these criminal enterprises are up to, the kind of attacks they frequently deploy, and the kinds of businesses they typically target.
State-sponsored actors and cybercriminals:
Collaboration between cybercriminals and nation-state threat actors is on the rise, and this is a risky development with broad ramifications. On the one hand, criminals can conduct sophisticated cyberattacks using the wealth of resources and talent that nation-states have access to. On the other hand, cybercriminals are more likely to be willing to sell their expertise to the highest bidder because they are motivated by money rather than politics.
It seems inevitable that there will be an increase in cases of highly sophisticated cybercrime in the future due to the interaction of these two elements. Businesses need to be extremely cautious about this trend since it has the potential to go beyond any security measures that unwary organisations may have in place.
Theft of intellectual property:
Theft of intellectual property and sensitive company information is the major contributor to the cost of cybercrime. Internet connectivity has created a wide new field for cybercrime, and IP theft extends much beyond the conventional government interest sectors, such as military technologies. Searching for rival products that steal market share from legitimate owners is one technique to gauge the expense of intellectual property theft. It can be devastating if hackers steal intellectual property, such as product designs, from a small or medium-sized business.
As rival items join the market, it could be an unanticipated source of lost revenue for large corporations. At least 25% of the cost of cybercrime is attributable to intellectual property theft, which also puts national security at risk when it includes military equipment.
For the victim, these losses may frequently be invisible. They still have access to the intellectual property that the thieves copied, so they may blame rising competition for a fall in sales rather than stealing.
SOME FACTS:
· Cybercrime has now surpassed illegal drug trafficking as a criminal moneymaker
· Cybercrime cases in India, registered under the IT Act, increased at a rate of 300 per cent between 2011 and 2014. In 2015, there were 11,592 cases of cybercrime registered in India
· Somebody’s identity is stolen every 3 seconds as a result of cybercrime
· Without a sophisticated security package, your unprotected PC can become infected within four minutes of connecting to the Internet.
The financial sector now faces greater cybersecurity threats, in part because the cyber threat environment is deteriorating. In particular, state-sponsored assaults on financial institutions are increasing in frequency, sophistication, and devastation.
The Technology and International Affairs Programme at Carnegie updates this timeline using information from BAE Systems’ Cyber Threat Intelligence team to stay abreast of the changing threat landscape. The timeline is not intended to capture every occurrence; rather, it is intended to highlight significant themes and show how the threat landscape is changing over time.
Effects of cybercrime by the year 2040:
Everything you mention is just a tool that a human could use to commit a cybercrime. Even the Dallas police thing that riled up the ethics of robots was just a human driving a remote-controlled robot. The robot made no decisions, drones, IoT devices, quantum computers—none of these things make their own decisions. AI might be a different story if it is really an autonomous thing by 2040 but even then, I certainly hope that it will have oversight and limitations put in place by humans.
Cyberwarfare: Using cyberattacks to harm or impair a foreign country’s military operations, political systems, or essential infrastructure is known as cyberwarfare. Physical violence could break out as a result of cyberwarfare, or the conflict could spread and become unstable. A cyberattack on a nuclear power plant, for instance, may result in a meltdown, and one on an air traffic control system, inplane disasters.
Cyberespionage: Using cyberattacks to steal or modify sensitive information from another entity is known as cyber espionage. Hackers, corporations, criminals, and state entities may all engage in cyber espionage. For instance, a cyberattack on a government organisation could reveal top-secret information, while a cyberattack on a research facility could result in the theft of intellectual property.
Cybersabotage: It is the use of cyberattacks to obstruct or interfere with another entity’s regular operations. Cybersabotage may be inspired by retaliation, rivalry, extortion, or activism. A cyberattack on a bank, for instance, may remove or transfer money, or one on a social media site could disseminate rumours or propaganda.
What can be done?
- Investment in defensive technologies—from device to cloud—as well as the uniform adoption of fundamental security measures—such as regular updating, patching, and open security architectures—remain vital. The most advanced defences are not necessary to protect against the majority of cybercrimes. The main parties responsible for this are businesses and customers.
- There is a need for increased international law enforcement cooperation, both with the private sector and other countries’ law enforcement agencies. However, this also means that there is a need for more funding for agency expansion, investigation, and the development of developing countries’ capacity to combat cybercrime.
- This involves enhancing current procedures like the MLAT (Mutual Legal Assistance Treaty). MLATs enable one government to ask for another’s assistance in tackling cybercrime or gathering proof. MLATS must be updated or replaced because they were designed for a time before the internet and are insufficient.
- We have frequently emphasised this report’s and previous studies’ importance of better aggregate data collected by national authorities.
- Security would be improved by more standardisation (threat data) and coordination of cybersecurity needs, especially in essential finance-related industries.
- Nation-states with insufficient cybercrime legislation have increased cybercrime rates and caused issues for their neighbours. A formal convention against cybercrime called the Budapest Convention establishes state obligations for enforcement and collaboration. Still, the Budapest Convention has made only sluggish progress in the face of opposition from Russia and other nations. The deal, according to Russia, is intrusive and may not have much of an interest in reducing Russian criminal organisations. Because they were excluded from the treaty’s talks, China, Brazil, and India declined to sign it.
- Any progress in lowering cybercrime will be slowed if a new convention is not negotiated right away.
Conclusion:
Governments, corporations, and people are all impacted by the significant and expanding issue of cybercrime. Due to advancing technology and its widespread use, cybercrime may cause even greater harm by the year 2040. Cyberterrorism, cyber espionage, cyber warfare, cybersabotage, and cyber fraud are just a few examples of the different ways that criminality online can manifest. These types of cybercrime may have detrimental outcomes, including monetary losses, reputational injury, legal repercussions, privacy violations, identity theft, data breaches, cyberattacks, and psychological suffering. Cybercrime may, however, be prevented and dealt with via teamwork and coordinated efforts. Increasing international cooperation and regulation, enhancing cybersecurity awareness and education, enacting more stringent security policies and procedures, creating better detection and response systems, and encouraging moral and ethical technology use are some methods to combat and minimise cybercrime.
Blackcoffer Insights 47: Lakshmi, M S Ramaiah University of Applied Sciences, Bangalore